DASH
 "Businesses that just suffered from data leaks and phishing attacks are consistently found to lack IT visibility before and after an attack. Benjamin Franklin said that if you fail to plan, you plan to fail, and not planning your mitigation protocols in the event of an attack sets you up to fail. One step to ensure visibility pre and post attack is to install a separate network monitoring tool; it reduces downtime, facilitates cyber forensic teams and supports auditing procedures."
"Businesses that just suffered from data leaks and phishing attacks are consistently found to lack IT visibility before and after an attack. Benjamin Franklin said that if you fail to plan, you plan to fail, and not planning your mitigation protocols in the event of an attack sets you up to fail. One step to ensure visibility pre and post attack is to install a separate network monitoring tool; it reduces downtime, facilitates cyber forensic teams and supports auditing procedures."
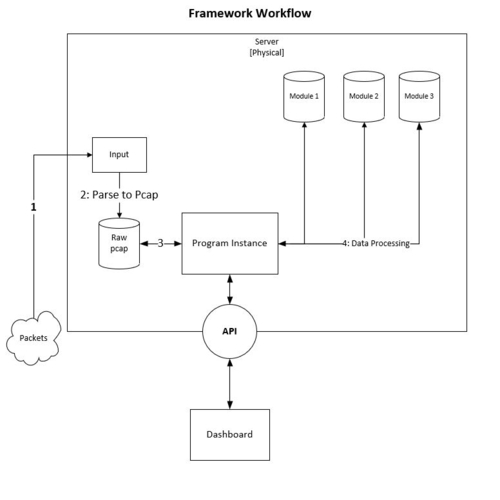
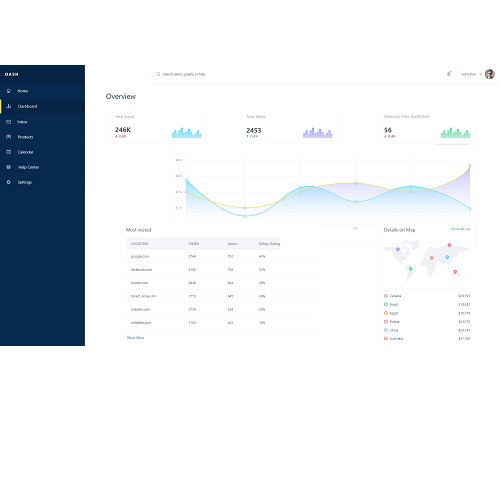
"It is impossible to devise mitigation strategies on your network if you cannot effectively monitor traffic patterns. DASH solves this problem by allowing companies to assess their network through modular tools such as a domain risk assessor, an external ownership classifier, and an internal ownership validator. The analysis and its insights are visualized and available to view as a front-end application. DASH is a free and open-source software tool."